How Continuous Threat Exposure Management (CTEM) Enhances Cyber Resilience
January 10, 2026

Introduction: Why Cyber Resilience Needs a New Approach
UK organisations are operating in an environment where cyber threats are no longer occasional shocks but a constant condition of doing business. Ransomware groups operate like professional enterprises. Supply chains are deeply interconnected. Cloud adoption has blurred traditional network boundaries. Regulatory pressure has increased, but so have attacker capabilities and speed.
In this reality, many organisations still rely on periodic security activities: annual penetration tests, quarterly vulnerability scans, and compliance-driven audits. While valuable, these point-in-time assessments cannot keep pace with the rate at which environments change or attackers adapt.
This is where Continuous Threat Exposure Management (CTEM) comes in.
CTEM is not a tool, a single product, or a compliance checkbox. It is a strategic, continuous discipline designed to help organisations understand, prioritise, and reduce their real-world cyber exposure — all the time.
When implemented properly, CTEM becomes a cornerstone of cyber resilience: the ability not just to prevent attacks, but to withstand, respond to, and recover from them with minimal operational impact.
This blog explores what CTEM really means, how it works, and why it is becoming essential for UK organisations seeking to improve cyber resilience and reduce breach risk.
What Is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management is a structured, ongoing process for identifying, evaluating, prioritising, and reducing cyber risk across an organisation’s entire attack surface.
Unlike traditional security approaches that focus on individual controls or isolated assessments, CTEM answers a more fundamental question:
How exposed are we to real attackers, right now — and what matters most to fix?
CTEM brings together multiple security activities into a single, continuous loop, including:
- External and internal attack surface discovery
- Vulnerability identification and validation
- Threat intelligence and adversary context
- Exposure prioritisation based on business impact
- Remediation tracking and verification
The keyword is continuous. CTEM assumes that exposure is always changing, because your organisation, technology stack, users, suppliers, and adversaries are always changing.
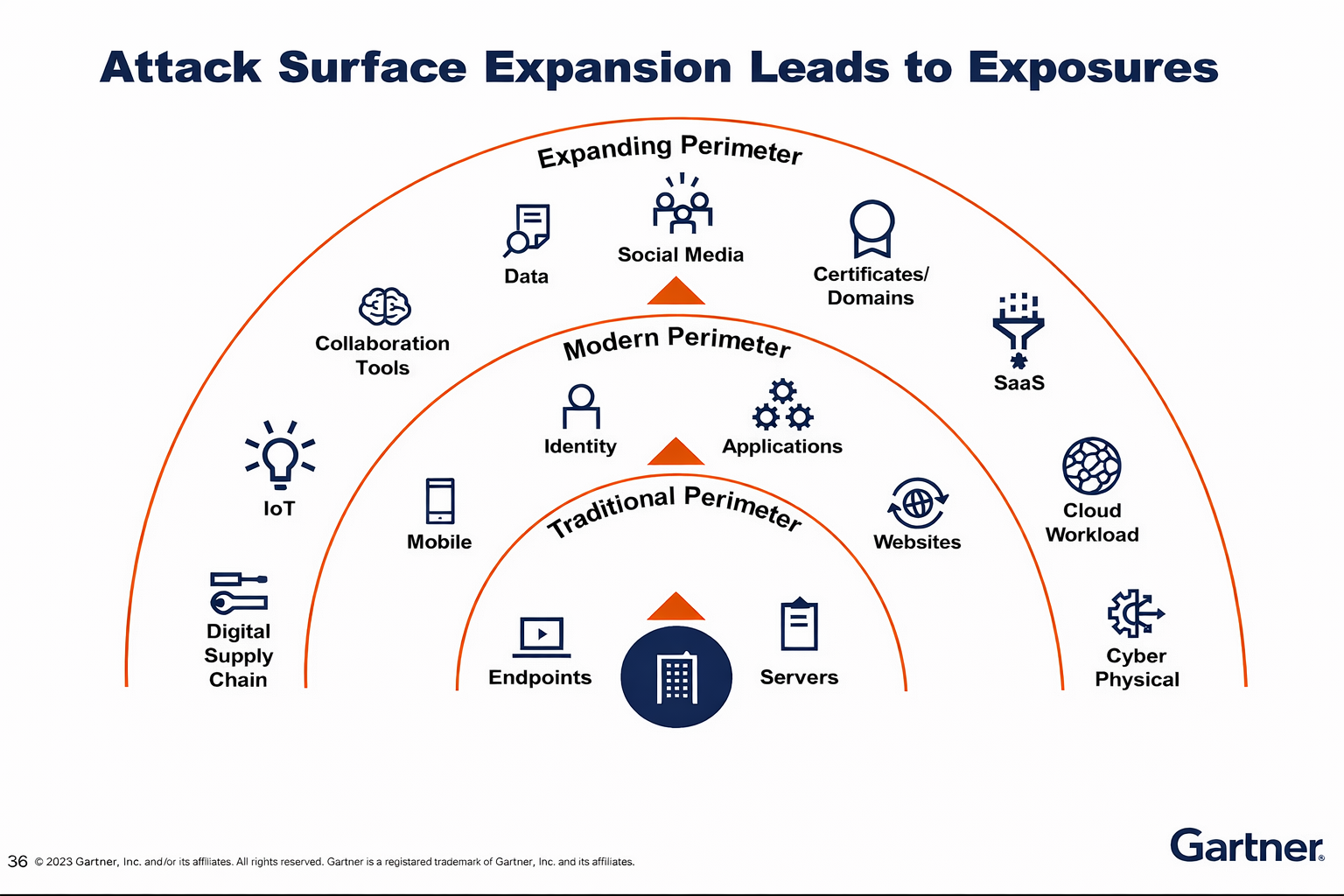
Understanding Cyber Resilience in the UK Context
Before exploring how CTEM enhances cyber resilience, it is important to clarify what cyber resilience actually means — particularly in the UK regulatory and operational environment.
Cyber resilience goes beyond traditional cybersecurity, which has historically focused on prevention. Instead, cyber resilience encompasses:
- Anticipation – understanding likely threats and exposures
- Resistance – implementing controls to reduce the chance of compromise
- Response – detecting and containing incidents quickly
- Recovery – restoring operations and learning from incidents
For UK organisations, cyber resilience is increasingly linked to:
- Business continuity and operational resilience requirements
- Sector-specific regulations (financial services, healthcare, critical infrastructure)
- Data protection obligations
- Board-level accountability for cyber risk
In short, cyber resilience is about ensuring that cyber incidents do not become existential business events.
CTEM directly supports this goal by focusing security effort where it reduces operational and business risk the most.
The Limitations of Traditional Security Models
To understand the value of CTEM, it helps to examine why many traditional security models struggle to deliver true resilience.
1. Point-in-Time Assessments
Annual penetration tests and periodic audits provide a snapshot of security posture at a single moment. In fast-moving environments, that snapshot can become outdated in weeks — sometimes days.
2. Vulnerability Overload
Traditional vulnerability management often produces thousands of findings, most of which are low risk or irrelevant in practice. Security teams become overwhelmed, leading to slow remediation and missed priorities.
3. Lack of Business Context
Many security programmes treat all vulnerabilities as equal, without considering:
- Whether an asset is internet-facing
- Whether it supports critical business services
- Whether attackers are actively exploiting similar weaknesses
4. Control-Centric Thinking
Organisations frequently measure security maturity by the number of tools deployed rather than by how effectively risk is reduced. More controls do not automatically equal better resilience.
CTEM addresses these challenges by shifting focus from theoretical risk to actual exposure.
The Core Principles of CTEM
At its heart, CTEM is built on a small number of powerful principles.
Continuous Visibility
You cannot manage what you cannot see. CTEM starts by continuously identifying assets, systems, applications, cloud services, identities, and dependencies — including those that may be unknown or unmanaged.
Threat-Led Prioritisation
CTEM prioritises exposures based on:
- Active threat intelligence
- Known attacker techniques
- Likelihood of exploitation
- Potential business impact
This ensures security teams focus on what attackers are most likely to exploit.
Business Alignment
CTEM aligns technical risk with business outcomes. A vulnerability affecting a critical revenue-generating system is treated very differently from one affecting a low-impact test environment.
Continuous Improvement
CTEM is not a one-off project. It is an ongoing cycle of measurement, action, and validation that continuously improves cyber resilience over time.
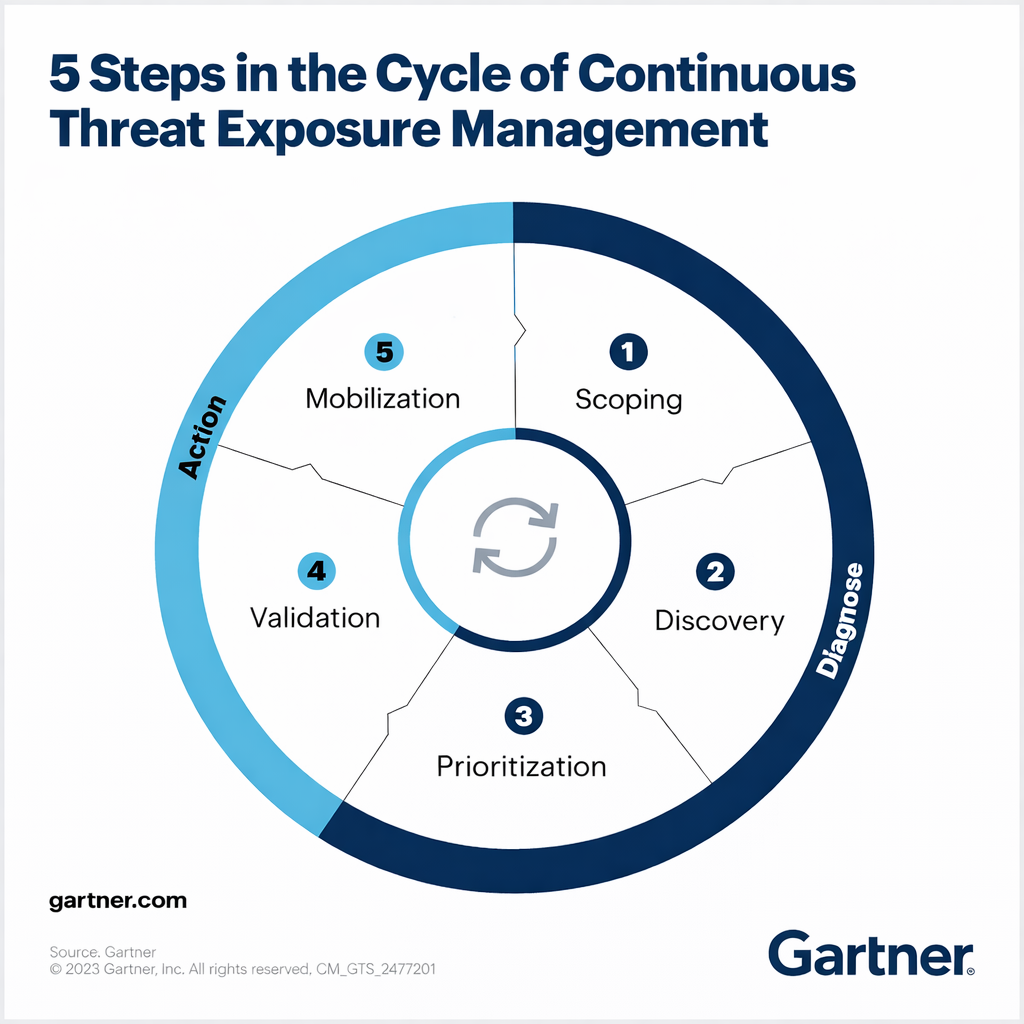
The CTEM Lifecycle: From Exposure to Resilience
While implementations vary, CTEM generally follows a structured lifecycle that repeats continuously.
1. Scoping and Asset Discovery
The first stage is understanding what needs protecting.
This includes:
- Internet-facing infrastructure
- Cloud environments and SaaS platforms
- Internal networks and endpoints
- User identities and privileged accounts
- Third-party connections and dependencies
In many organisations, this stage alone uncovers significant hidden exposure — forgotten systems, shadow IT, misconfigured services, or legacy assets still accessible from the internet.
2. Exposure Identification
Once assets are known, CTEM identifies exposures such as:
- Vulnerabilities
- Misconfigurations
- Excessive permissions
- Weak authentication controls
- Insecure APIs
- Outdated software and services
Unlike traditional scanning, CTEM treats exposure broadly — not just software flaws, but anything that increases the likelihood or impact of compromise.
3. Threat Contextualisation
This is where CTEM becomes transformative.
Exposures are enriched with:
- Intelligence on active threat actors
- Known exploitation trends
- Tactics, techniques, and procedures (TTPs)
- Industry and regional targeting patterns
For UK organisations, this often highlights threats targeting specific sectors such as finance, healthcare, manufacturing, education, and local government.
4. Risk-Based Prioritisation
CTEM then answers the critical question:
Which exposures actually matter most right now?
Prioritisation considers:
- Exploitability
- Asset criticality
- Business service dependency
- Regulatory and legal impact
- Potential operational disruption
This prevents wasted effort on low-risk issues and enables focused, high-impact remediation.
5. Remediation and Mitigation
Security teams, IT operations, and business stakeholders work together to:
- Patch vulnerabilities
- Harden configurations
- Reduce attack surface
- Implement compensating controls
CTEM encourages pragmatic risk reduction, not perfection.
6. Validation and Continuous Monitoring
Finally, CTEM validates that remediation efforts have actually reduced exposure, and continues monitoring for new risks as environments change.
The cycle then repeats.
How CTEM Directly Enhances Cyber Resilience
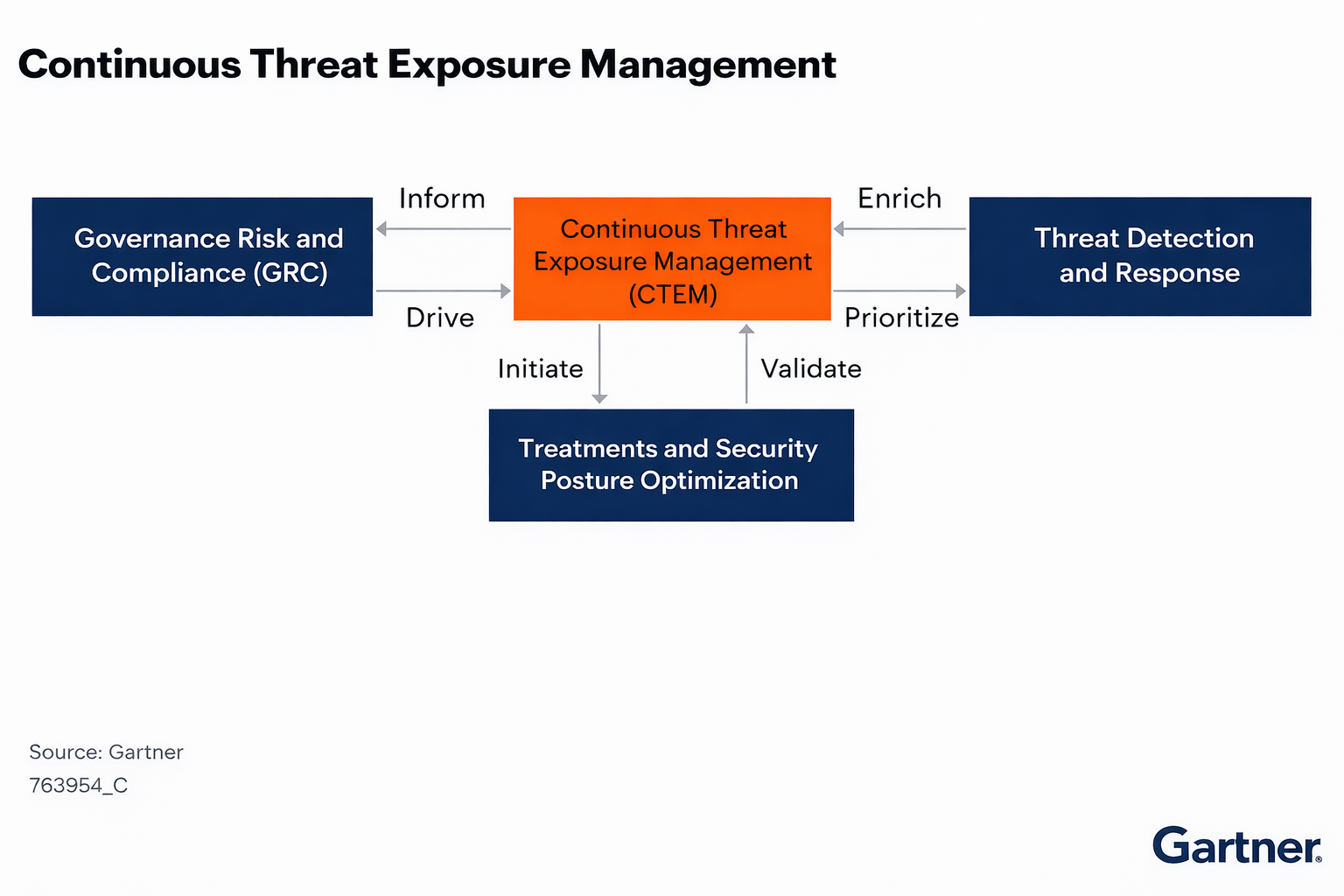
CTEM strengthens cyber resilience in several fundamental ways.
1. Reducing the Likelihood of Successful Attacks
By continuously identifying and prioritising exploitable exposures, CTEM reduces the number of viable attack paths available to adversaries.
Attackers thrive on:
- Unpatched systems
- Misconfigured services
- Over-privileged accounts
CTEM systematically removes these opportunities before they can be exploited.
2. Improving Detection and Response Readiness
CTEM provides a deep understanding of where attacks are most likely to occur. This insight improves:
- Detection rule tuning
- Alert prioritisation
- Incident response planning
When an incident does occur, teams are better prepared because they already understand their highest-risk assets and exposures.
3. Minimising Blast Radius
Not all breaches can be prevented. Cyber resilience depends on limiting damage.
CTEM helps organisations:
- Identify critical choke points
- Reduce unnecessary connectivity
- Enforce least privilege access
This limits lateral movement and reduces the impact of successful intrusions.
4. Enabling Faster Recovery
Because CTEM aligns security priorities with business services, organisations know:
- Which systems must be restored first
- Which compromises pose the greatest operational risk
- Where resilience investments deliver the most value
This accelerates recovery and reduces downtime.
CTEM and UK Regulatory Expectations
While CTEM is not itself a regulatory requirement, it aligns closely with UK regulatory expectations around risk management and operational resilience.
Board-Level Accountability
UK regulators increasingly expect boards to:
- Understand cyber risk in business terms
- Make informed investment decisions
- Demonstrate ongoing oversight
CTEM provides clear, prioritised insights that support board-level reporting and decision-making.
Risk-Based Security Management
Regulatory frameworks emphasise proportional, risk-based approaches rather than blanket controls. CTEM embodies this philosophy by focusing on material risk reduction.
Continuous Assurance
Point-in-time compliance is no longer sufficient. CTEM supports continuous assurance by maintaining an up-to-date view of exposure and risk.
CTEM vs Traditional Vulnerability Management
It is important to distinguish CTEM from conventional vulnerability management, as the two are often confused.
| Traditional Vulnerability Management | CTEM |
|---|---|
| Periodic scans | Continuous visibility |
| CVSS-driven prioritisation | Threat- and business-led prioritisation |
| Tool-centric | Process- and outcome-centric |
| Large volumes of findings | Focused, actionable insights |
| Limited business context | Strong alignment to business impact |
CTEM does not replace vulnerability management — it elevates it into a strategic discipline that directly supports cyber resilience.
Common Misconceptions About CTEM
“CTEM Is Just Another Tool”
CTEM is not a single product. Tools may support CTEM, but the value comes from the process, governance, and decision-making it enables.
“CTEM Is Only for Large Enterprises”
While large organisations often adopt CTEM first, the principles apply equally to UK SMEs. In fact, organisations with limited resources often benefit the most from better prioritisation.
“CTEM Replaces Penetration Testing”
CTEM complements, rather than replaces, penetration testing. Pen testing provides depth and adversarial insight; CTEM ensures findings are contextualised and acted upon continuously.
Practical Steps to Implement CTEM
1. Start With Clear Objectives
Define what cyber resilience means for your organisation:
- Reduced downtime?
- Protection of critical services?
- Regulatory confidence?
CTEM should support these outcomes, not exist in isolation.
2. Establish Ownership and Governance
CTEM requires cross-functional collaboration between:
- Security
- IT operations
- Risk management
- Business leaders
Clear ownership ensures momentum and accountability.
3. Focus on Visibility First
Many CTEM initiatives fail because they attempt to prioritise risk before understanding the environment. Invest early in comprehensive asset and exposure visibility.
4. Integrate Threat Intelligence
Threat context transforms raw exposure data into meaningful risk insight. Intelligence should inform prioritisation, not sit in separate reports.
5. Measure What Matters
Success metrics should focus on:
- Reduction in exploitable exposure
- Time to remediate critical risks
- Improved incident response outcomes
Avoid vanity metrics that do not reflect real risk reduction.
The Strategic Value of CTEM for Cyber Resilience
CTEM delivers value far beyond technical security improvements.
For Executives
- Clear visibility of cyber risk
- Better investment decisions
- Increased confidence in resilience posture
For Security Teams
- Reduced alert and vulnerability fatigue
- Clear priorities
- Stronger alignment with business goals
For the Organisation
- Fewer disruptive incidents
- Faster recovery when incidents occur
- Greater trust from customers and partners
The Future of CTEM and Cyber Resilience in the UK
As cyber threats continue to evolve, static security models will become increasingly ineffective. UK organisations face growing pressure to demonstrate not just compliance, but resilience.
CTEM represents a shift from:
- Reactive to proactive
- Theoretical risk to real exposure
- Tool accumulation to outcome-driven security
Organisations that adopt CTEM now will be better positioned to withstand the cyber challenges of the coming years.
Summary: CTEM as a Foundation for Resilient Security
Cyber resilience is not achieved through single controls, annual assessments, or compliance exercises. It is built through continuous understanding, prioritisation, and reduction of exposure.
Continuous Threat Exposure Management provides the structure and discipline needed to achieve this at scale.
For UK organisations seeking to reduce breach risk, protect critical services, and operate with confidence in an increasingly hostile digital environment, CTEM is no longer optional; it is foundational.
By embracing CTEM, organisations move beyond asking “Are we secure?” and begin answering the far more important question, "How do we remain secure?".
Reference: Gartner (2024)
Ready to strengthen your security posture? Contact us today for more information on protecting your business.
Let's get protecting your business
Thank you for contacting us.
We will get back to you as soon as possible.
By submitting this form, you acknowledge that the information you provide will be processed in accordance with our Privacy Policy.
Please try again later.
Cybergen News
Sign up to get industry insights, trends, and more in your inbox.
Contact Us
Thank you for subscribing. It's great to have you in our community.
Please try again later.
SHARE THIS
Latest Posts